CompTIA Network+ Exam Pro iOS and Android App
Boost Your Networking Know-How!
Introducing CompTIA Network+ Exam Pro — the ultimate app to help you crush the CompTIA Network+ (N10-008 & N10-009) certification. Whether you're starting out in networking or looking to sharpen your skills, this app has everything you need to stay ahead in the fast-paced world of IT infrastructure.
Explore an extensive collection of questions that cover all the critical areas of the Network+ exam, from network infrastructure and routing to security protocols, cloud technology, and troubleshooting. Each question comes with in-depth explanations, giving you not just the what but the how behind every solution.
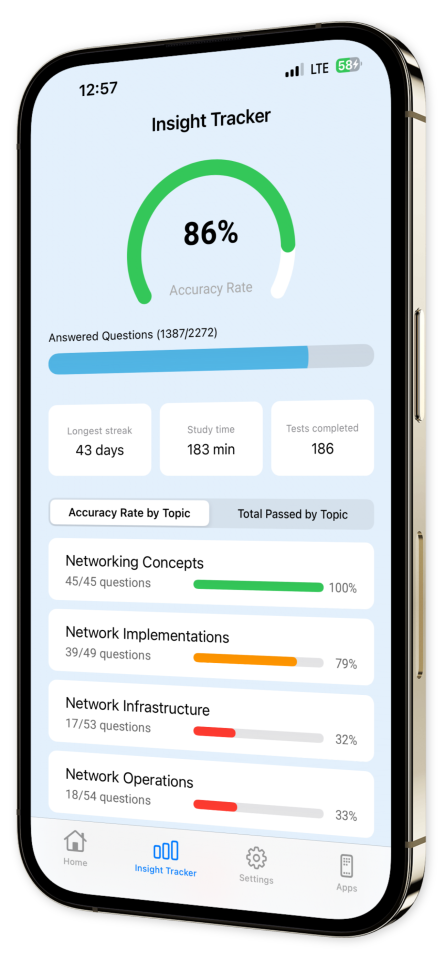
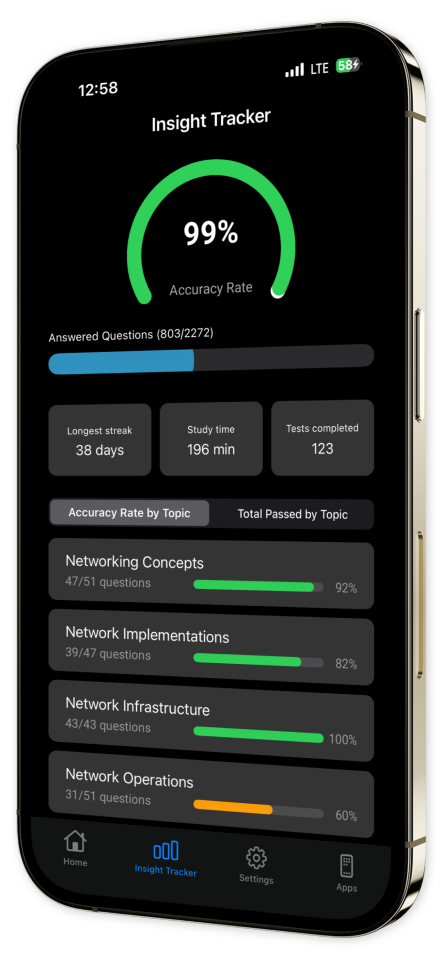
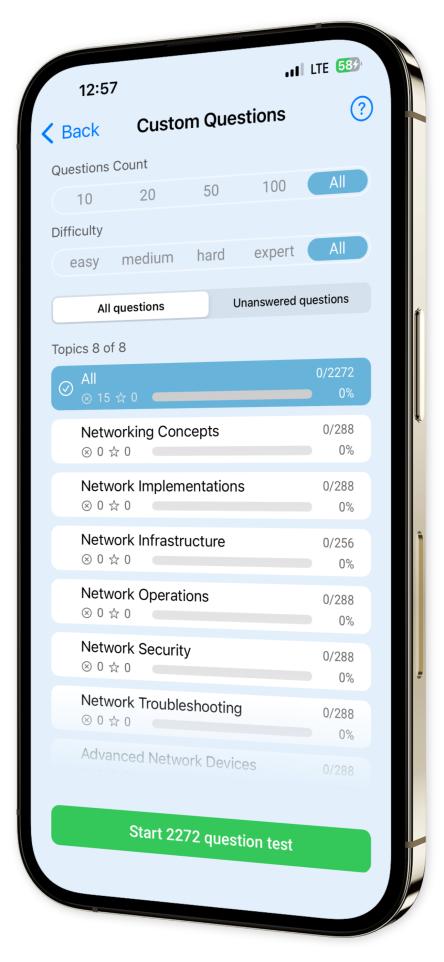
Create custom assessments based on specific topics like IP addressing, wireless networking, or troubleshooting, and focus on building the expertise that matters to you. Track your progress and create a personalized collection of challenging questions to practice and perfect before test day.
Thousands of IT pros are already leveraging CompTIA Network+ Exam Pro to solidify their networking knowledge. Build your confidence, get certified, and set yourself up for success in the IT networking world. Download now and start your journey to becoming a networking pro!
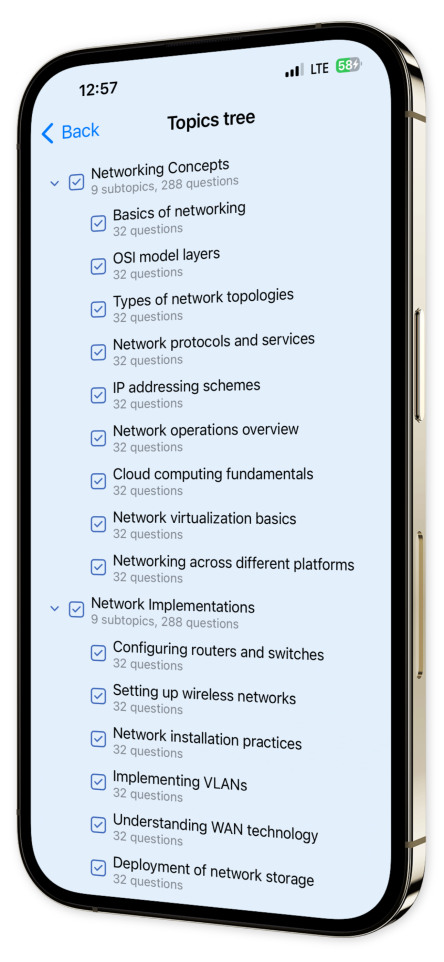
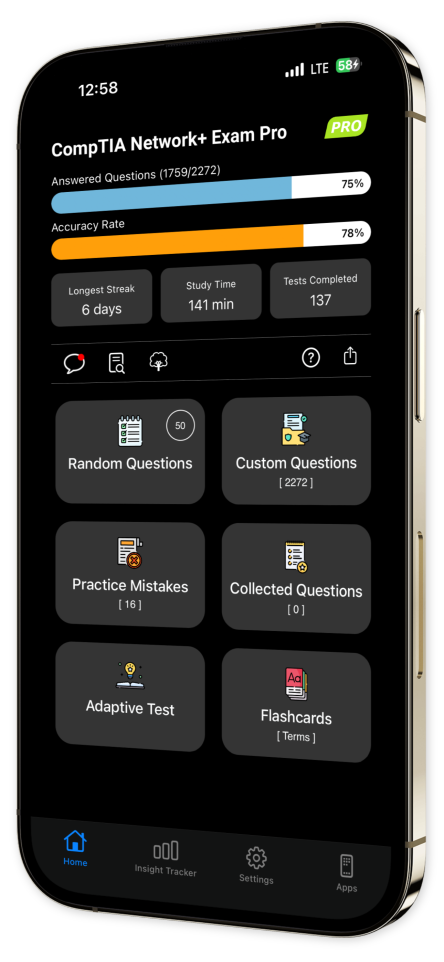
Content Overview
Explore a variety of topics covered in the app.
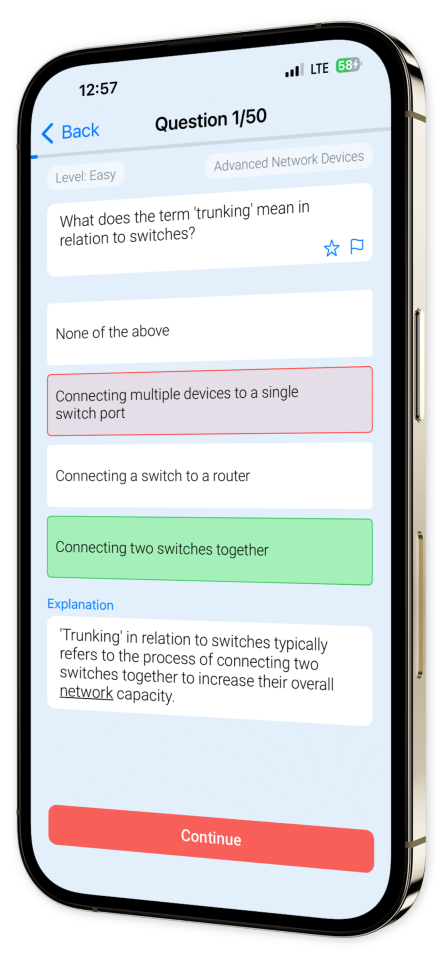
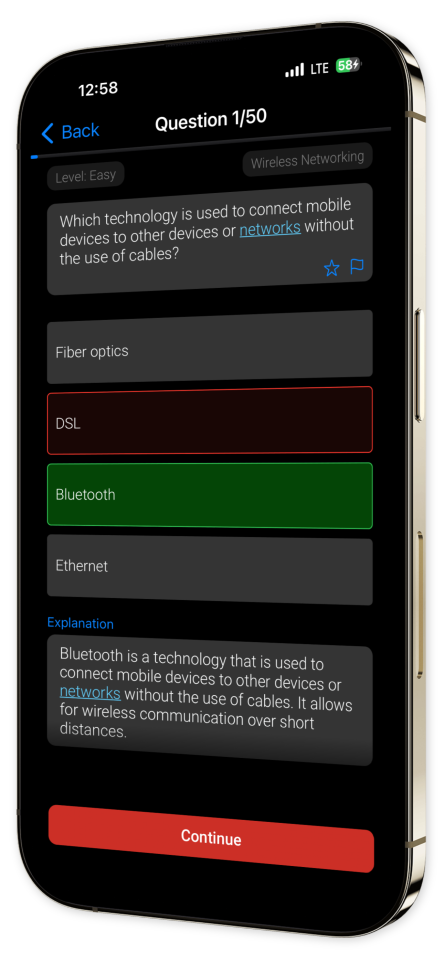
Example questions
Let's look at some sample questions
Which layer of the OSI model is responsible for converting data into a format that the application layer can understand?
Presentation LayerSession LayerTransport LayerNetwork Layer
The Presentation Layer (Layer 6) of the OSI model is responsible for converting data into a format that the application layer can understand.
Which protocol is used to send email messages from a mail client to a mail server?
POP3IMAPSMTPFTP
Simple Mail Transfer Protocol (SMTP) is used for sending email messages from a client to a server.
Which tool is commonly used for version control in network configuration management?
WiresharkGitPingNmap
Git is a commonly used tool for version control in network configuration management. It allows tracking changes to network configurations and revert to previous versions if needed.
How does Network Asset Monitoring contribute to security?
By controlling access to assetsBy detecting unauthorized accessBy encrypting dataBy providing VPN services
Network Asset Monitoring contributes to security by detecting unauthorized access to the network assets. It helps in identifying potential security threats and taking appropriate actions.
Which protocol is used for automatic IP address assignment on a network?
HTTPDHCPFTPTCP
Dynamic Host Configuration Protocol (DHCP) is used for automatic IP address assignment on a network. It dynamically distributes network configuration parameters, such as IP addresses.
Which regulation requires financial institutions to explain how they share and protect their customers' private information?
GLBAHIPAAFISMASOX
The Gramm-Leach-Bliley Act (GLBA) requires financial institutions to explain how they share and protect their customers' private information.
What type of attack involves an attacker secretly relaying and possibly altering the communication between two parties who believe they are directly communicating with each other?
Man-in-the-middle attackPhishing attackBrute force attackSQL injection attack
A man-in-the-middle attack involves an attacker secretly relaying and possibly altering the communication between two parties who believe they are directly communicating with each other.
What step follows after identifying a probable cause in network troubleshooting methodology?
Establishing a plan of action to resolve the problemIdentifying the symptoms and problemsTesting the theory to determine the causeDocumenting findings, actions, and outcomes
After establishing a theory of probable cause, the next step is to test this theory to determine whether it is indeed the cause of the problem.
Which of the following is not a function of an aggregation switch?
Load balancingPacket filteringTraffic shapingDynamic routing
Aggregation switches are primarily used for load balancing, packet filtering, and traffic shaping. Dynamic routing is typically handled by routers or layer 3 switches, not aggregation switches.
Why is data encryption important in IoT networks?
To increase data storage capacityTo improve data transfer speedTo protect data from unauthorized accessTo reduce power consumption
Data encryption is important in IoT networks to protect sensitive data from unauthorized access. It ensures that even if data is intercepted, it cannot be read without the correct decryption key.